I’m now using an offline network behind a data diode for several years. The data diode allows only transferring data from the internet into the offline network, but there is no back channel to the internet. Since I switched from a serial to a fiber optics connection, the speeds are suitable for day to day use. In this post I want to share my use cases and experiences.
My goals of using an offline network:
- Securely creating and storing private keys, for example PGP. The private keys are copied to hardware security modules (Yubikeys/Nitrokeys) for online usage.
- Backup of highly important data, for example .kdbx files.
- Offline knowledge management for very private information.
Overview of my network topology:
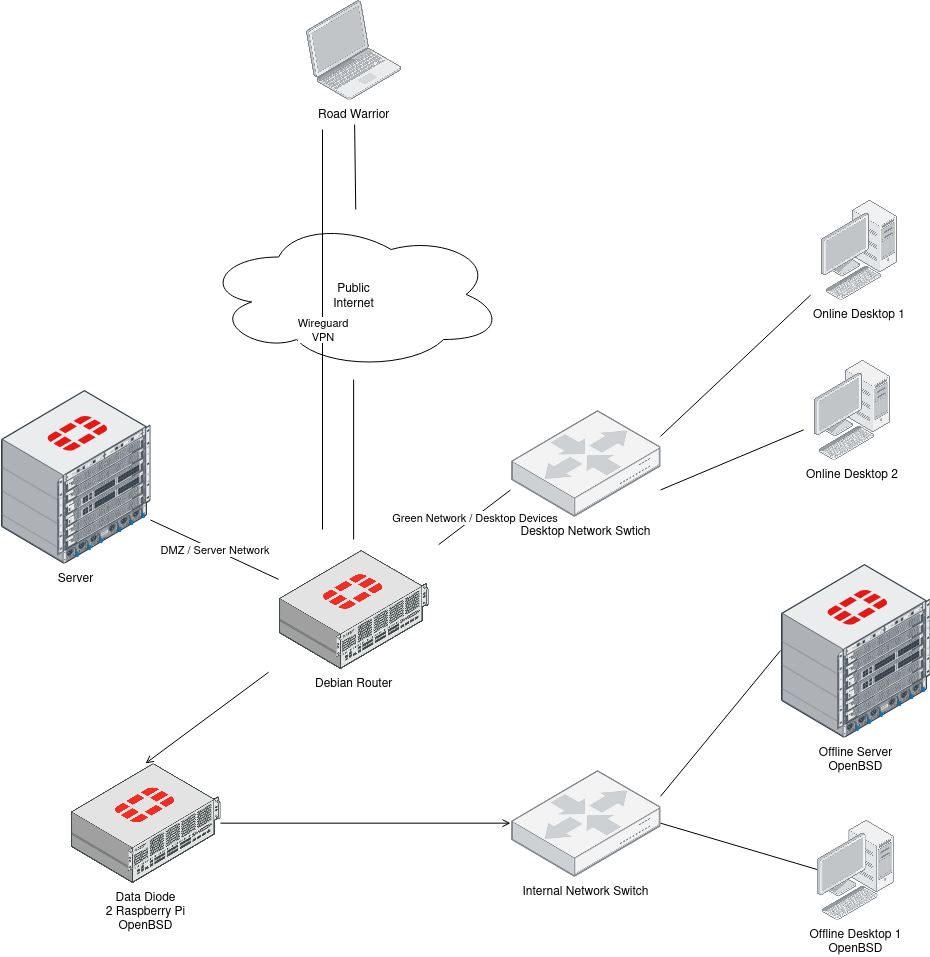
I generally use sshfs to transfer data between the devices in the online and internal offline network.
- In the online network, the desktop devices use sshfs to mount the “send” directory of the public facing Raspberry Pi of the data diode.
- In the offline network, the desktop devices use sshfs to mount the “receive” directory of the internal facing Raspberry Pi of the data diode.
- Additionally, the internal facing Raspberry Pi runs the OpenBSD httpd server to serve a mirror of the OpenBSD install, syspatch, packages and firmware directories for the amd64 and arm64 architectures.
In the offline network, I currently use the following OpenBSD packages for a very light weight setup:
- Zim for managing information
- git for versioning the Notebook directories created by Zim
- sshfs for mounting the diode directories
- KeePassXC for reading and managing kdbx backups and secrets that are only stored in the offline network
- mc (Midnight Commander) for managing files
- i3 with i3lock and i3status as a desktop manager
- gnupg for managing PGP keys
My experiences so far:
- The data diode speed of about 0.5 MB/s is sufficiently fast to transfer OpenBSD updates and the limited set of packages in a reasonable amount of time into the internal network. It takes me 1 to 2 hours to download and transfer all files for a new OpenBSD major release.
- I rarely have issues with OpenBSD in the offline network. Managing a mirror with all required files and packages does not require a lot of effort. I use the normal tools (sysupgrade, syspatch, pkg_add, fw_update) to manage the software.
- The offline desktop devices uses the OpenBSD full disk encryption. As I have a screen and a keyboard, I can directly unlock the disk during boot.
- The offline server only encrypts the /home directory so that it can boot without me attending the process. To mount the /home partition, I enter the disk password via SSH from a desktop device.
- I use the /home directory on the internal server as a backup destination for the files I work with on the offline desktop devices:
- git repos are directly synchronized with git push
- other files are copied via sshfs and mc
- I boot up the devices in the offline network only a few times a year. This usually happens when I need to rotate keys, create backups of new important secrets, or update the OpenBSDs in the internal network.
